
Trick or treat: I know your password!
A few months ago, some rather creative hackers came up with a pretty ingenious con. They realized they could create an email like the one below pretending to have hacked your computer and installed malware that has allowed them to watch you surf the internet and even video what you were doing while surfing the internet. The challenge though is if I were to email you and say “I hacked your computer and I know your passwords and I watched you visiting websites and even recorded video of you doing so” would you believe me? Probably not. But what if I told you “and not only do I know your email address, but I also know your password and it’s … YOURPASSWORDHERE” and it was a password you’ve used in the past? That would be a lot more credible right?
In fact, here’s such an email:
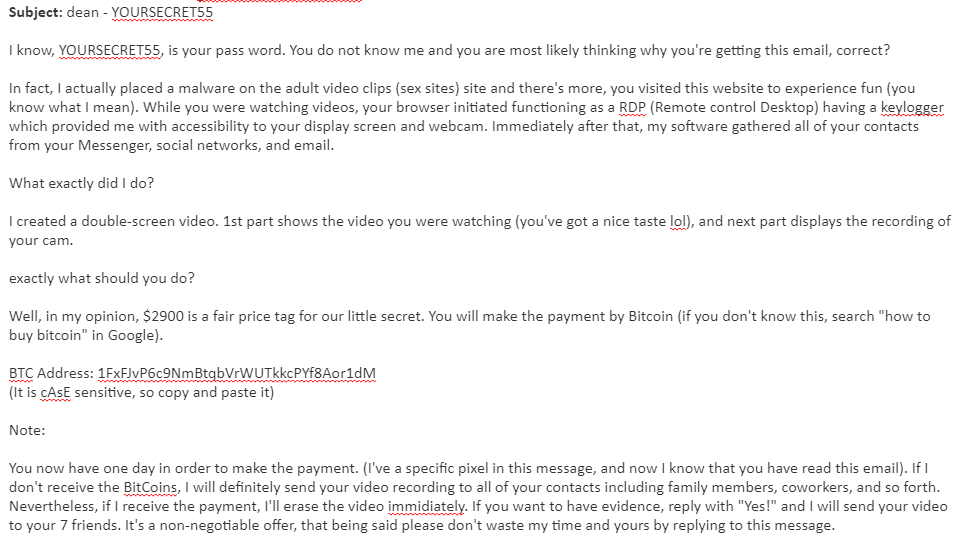
Or Maybe this one:
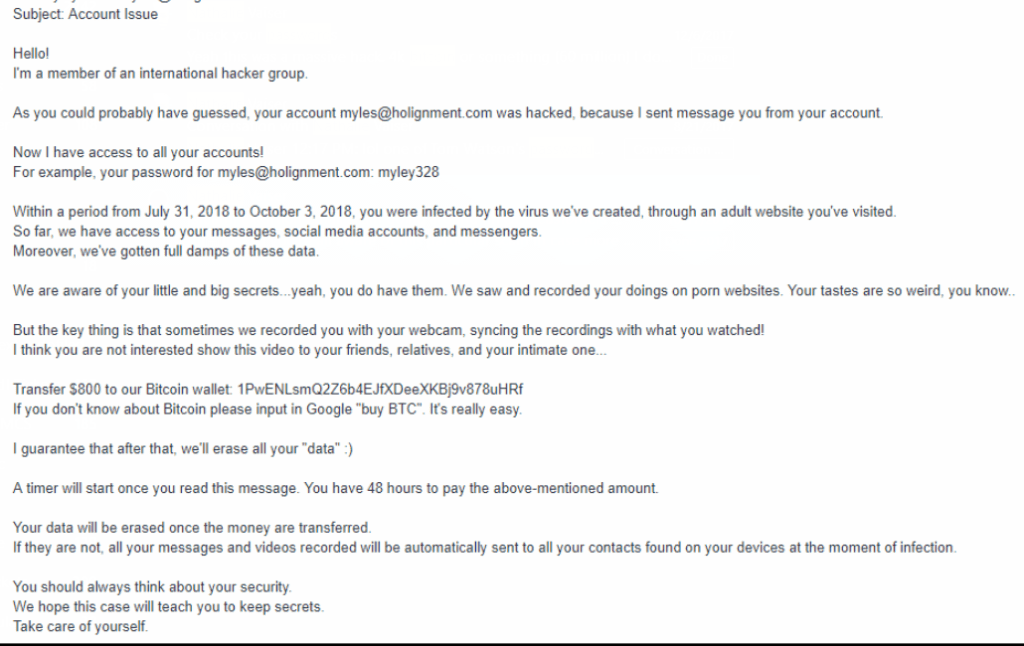
Or perhaps this one:

Now let’s assume one of the password mentioned in the email was actually the password you used on LinkedIn, MySpace, Yahoo, Twitter, Dropbox, Elance, Coindesk or even Naughty American (hey we’re not judging here) would you feel compelled to think the threat was credible? Maybe, maybe not. But thanks to these hackers sharing their bitcoin addresses, we’re able to use a bitcoin tracker and see if it worked! So let’s check some of the bitcoin addresses above:
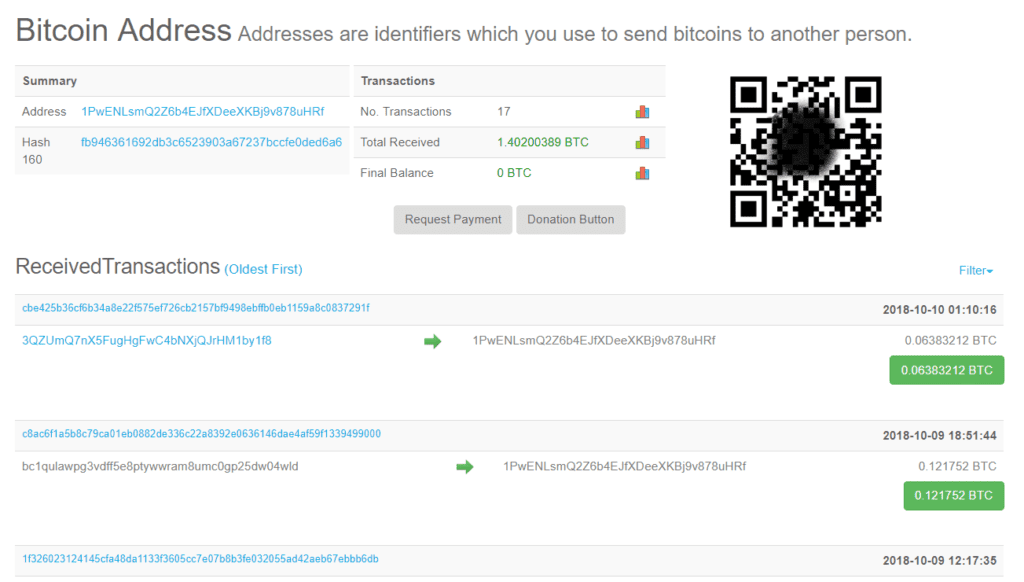
- 1PwENLsmQ2Z6b4EJfXDeeXKBj9v878uHRf – This guy had 17 transactions (15 deposits, 2 withdrawals) for a total of 1.4 bitcoin or roughly $6000 today.
- https://www.blockchain.com/btc/address/1JC99fcQMVR4iHdmf3GbHLGHMkPpyFjBu7 – this guy, not so much.
- https://bitref.com/1FxFJvP6c9NmBtqbVrWUTkkcPYf8Aor1dM – This guy ½ a bitcoin or about $2000 at today’s prices.
- https://bitref.com/1L8WkXH3q1aeCj4MEHj5Szr5upuz1tomKx – This our most recent hacker and I’m pleased to say he didn’t have any luck (yet).
Am I really hacked? How did they know my passwords?
Here’s the good news, although this guy might know a password you’ve used (or are using today) they probably didn’t hack into your computer, they probably didn’t monitor your websurfing and they probably aren’t spying on you, using your own webcam. Not to say those things can’t happen because they can. But here’s where the ingenious part comes into play. Any time there’s massive password leak, it makes the news, like this LinkedIn leak in 2016 in fortune: http://fortune.com/2016/05/18/linkedin-data-breach-email-password/. A real hacker would know how to access that data and then could create an email script to email everyone on that list. Another way though is that there are websites like: haveibeenpwned.com, dehashed.com, leakprobe.net and scatteredsecrets.com that provide you the ability to search those lists without having to know how to get those lists. So a hacker could just query those services and pull that same information (until recently when they started making it harder to just get the information). So there you have it, that’s how this ‘hacker’ got your email address and how they actually knew a password you used in the past.
How do I protect myself from this happening to me?
The next obvious question is “how do I protect myself from this happening to me?” well it’s really password common sense these days but not many people follow it so let’s break it down:
- Don’t use the same password for multiple websites/services and use strong passwords. I know what you’re thinking “If I use a password like: lMAvJ!38ikpI” then how do you expect me to remember that password? Well you won’t! But if you use a password manager then you won’t have to. I’ve used lastpass.com for several years now and have to remember one password, the password for lastpass and everything else is stored in lastpass. The best thing is all of my sites use different strong passwords and if there’s a leak lastpass even notifies you and in most cases is able to rotate your password for you from within the application.
- Do a “Dark Web” Scan it’s like a credit score check for your password. There are several websites that allow you to do this online for free and many that do it for a fee. You can also schedule a 1 on 1 consultation with one of the AppliedI team members and we’ll perform one for your entire domain name as well as your personal email addresses for you. BTW, If you’re wondering what the hell is the Dark Web, it’s a marketing buzz word for the networks, websites, etc that hackers use to share information. The “Dark Web” oooohhh scary!
- Monitor your “Dark Web” Exposure. Just like there’s a credit score check, there’s also credit score monitoring, and we can continuously monitor your domain and personal email addresses for exposure on the Dark Web and send you a notification when something is picked up. Schedule the one on one consultation and we’ll be happy to go over options here with you.
- Stop using weak passwords and the same password on multiple websites. I know we covered that one already, but it’s actually two tips and it bears repeating. So stop doing it, right now!
- Multi-factor Authentication (MFA) is a must. What is that you ask? You’re probably using already today with your bank account, when you log into the bank with your username and password it sends you a text message that you must verify by typing in the code on their website to gain access to your account. This helps avoid password compromises because even if someone has your password, they would also need your phone to get that security code in order to gain access to your account. Key services you need to implement this on today include: Domain Registrar accounts, Email Accounts (it’s included for free with Office 365) and services that store passwords and personal information like google cloud and apple’s icloud. If you don’t know how to set this up, you can enter the website here: https://twofactorauth.org/ or here https://www.turnon2fa.com/tutorials/
There’s the first 5 tips for you and if you just did those 5 things, you’d be in much better shape than your peers today, but we’re not done there. I’ve put together “The executives guide to modern cloud security” as a simple to understand checklist of some tactics you should employ today to better protect yourself, your company and your employees and it’s available exclusively to you by simply filling out the form below. Best of all, it’s setup in a simple checklist format so you can review it with your IT staff to ensure you’re covering the basics.
