
Zero-Day Zoom Webcam Vulnerability targeting Apple Macs announced
Apple Macbooks and iMacs have been long praised for their built-in security features and access restrictions, unfortunately, the software you install on your Macbook, not so much!
Yesterday, Jonathan Leitschuh provided a post on Medium, the popular blog aggregation service, about a zero-day vulnerability in Zoom’s Conferencing software the opens your Apple MacOS computer to potential exploitation allowing, among other things, hackers to remotely activate your webcam by simply having you visit a website with specially crafted code on the site.
Jonathan goes through great detail about how he discovered the vulnerability, how he alerted Zoom of the issue and then how the vulnerability, 90 days later, still remains open. You can read the entire post in detail at Zoom Zero Day: 4+ Million Webcams & maybe an RCE? Just get them to visit your website!
What’s most troubling about this vulnerability is that even if you remove zoom from your Mac, remnants remain, namely a web server running on your desktop, that can still be exploited. This means even if you completely uninstall Zoom from your Mac today, you are still vulnerable. It’s a great read and highly recommended
TL;DR How To Protect Myself
The “Too Long; Didn’t Read” excerpt for those that want to protect themselves is pretty straight forward, just turn off the webcam when joining zoom meetings by default:
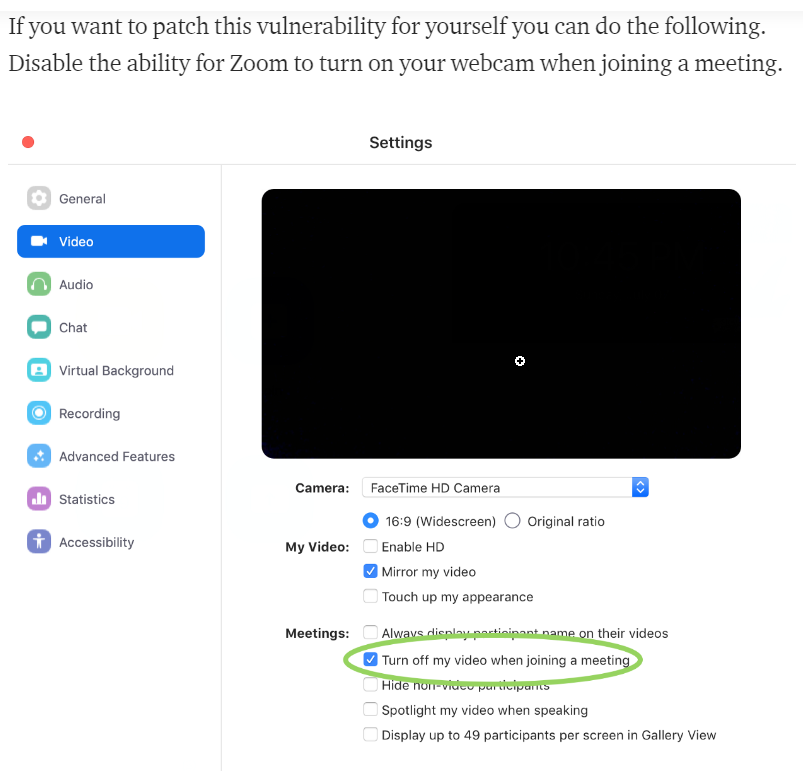
Jonathan also shared that you can disable this for all users by opening a terminal window and copy and pasting:
sudo defaults write /Library/Preferences/us.zoom.config.plist ZDisableVideo 1
Lastly, if you installed zoom and removed it recently you still have the web service installed. The best way to remove that web service is outlined in his article:
To shut down the web server, run lsof -i :19421 to get the PID of the process, then do kill -9 [process number]. Then you can delete the ~/.zoomus directory to remove the web server application files.
To prevent this server from being restored after updates you can execute the following in your terminal:
rm -rf ~/.zoomus touch ~/.zoomus
What else can I do?
So let’s face it as business owners, leaders, executives and managers we live in precarious times. Hackers are targeting small to medium-sized businesses more aggressive because they’ve found small to medium-sized businesses aren’t adequately protected, have increased fear because they know they aren’t adequately protected and because of all of this are the most likely to pay ransoms!
So your best approach? Step up your game. We’ve built a simple cybersecurity checklist for executives (so easy even you can do it) that helps you review your current exposure to risk and take proactive steps to minimize it. So as a responsible business owner, executive, leader or manager downloading that list should be your next step.
